Let us mitigate Sitecore SOLR Log4J vulnerability with ease
Introduction
Log4J Security Alert addresses CVE-2021-44228, a remote code execution vulnerability in Apache Log4j. It is remotely exploitable without authentication, attackers can remotely run any code to gain access to all data on the affected machine. It also allows them to delete or encrypt all files on the affected machine and store them for a ransom demand. This potentially makes it a target for anything that uses a vulnerable version of Log4j. In most of the Sitecore SOLR servers will be internal only but the security team scans would flag them and its always safe to be patched.
Sitecore
Security Bulletins - Security Bulletin SC2021-004-511605
SOLR
Solr™ Security News - Apache Solr
MSFT
Microsoft’s Response to CVE-2021-44228 Apache Log4j 2 – Microsoft Security Response Center
Log4J
https://logging.apache.org/log4j/2.x/security.html
SearchStax
https://www.searchstax.com/blog/how-searchstax-is-handling-cve-2021-44228-log4j-vulnerability/
Sitecore
Sitecore is not directly affected, but the SOLR instance that is being used for search is affected.
Affected
Sitecore 9.2 and above are affected. Installing a new instance we are expected to patch it.
Not Affected
Sitecore 9.1 and below
SearchStax hosted SOLR
Coveo Search
Mitigation
Best option is to upgrade to SOLR 8.11.1 or greater but Sitecore has strict version compatiblity requirement with SOLR and at the time of writing 10.2 uses SOLR 8.8.2
There are multiple options only two can be used with Sitecore SOLR.
Option 1: Manually update the Log4J runtime
I will walk through the steps for a standalone SOLR instance for Sitecore 10.2 with SOLR 8.8.2. It should be similar for other version. Test the process on your dev instance and ensure it works as expected.
Download the patched version for updating and extract it to a folder
https://archive.apache.org/dist/logging/log4j/2.17.1/apache-log4j-2.17.1-bin.zip
Stop the SOLR Service (Open run prompt and type services.msc)
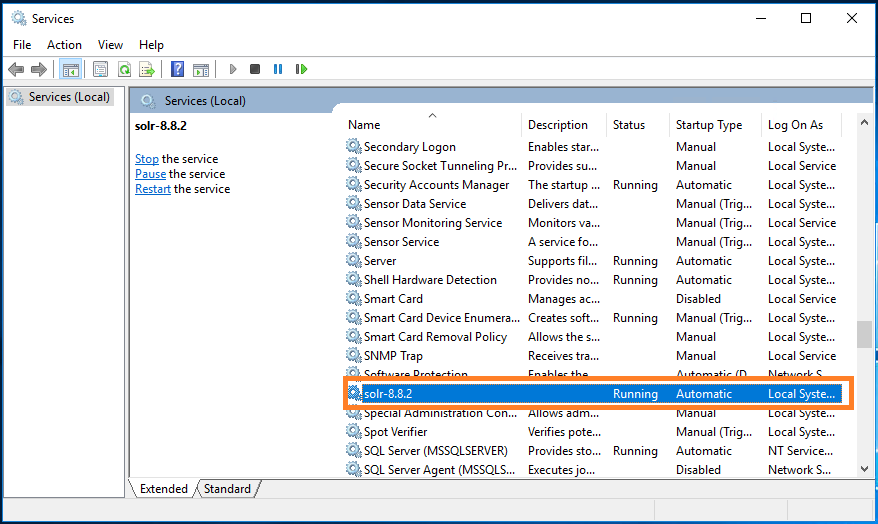
Backup the SOLR folder from your installation location in my case it is c:\solr
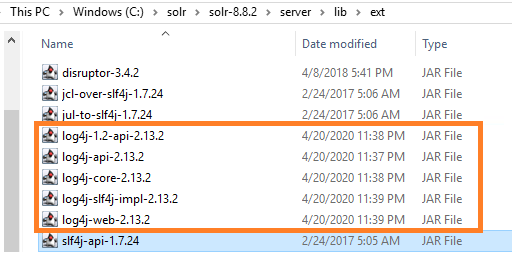
Delete the older version log4j files in the following locations and replace with the new version that we downloaded
c:\solr\solr-8.8.2\server\lib\ext
c:\solr\solr-8.8.2\contrib\prometheus-exporter\lib
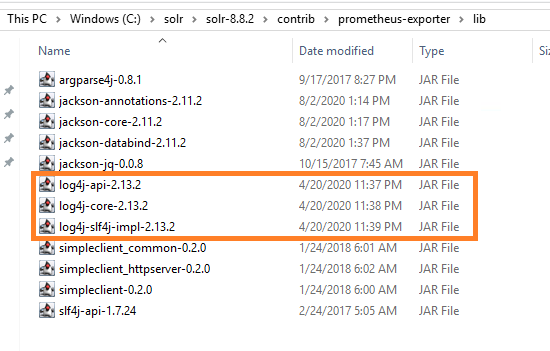
Start the service and check if SOLR starts and working as expected.Ensure you do some search in Sitecore content editor also monitor SOLR logs.
Option 2: Edit solr.in.cmd file
Stop the SOLR Service (Open run prompt and type services.msc)

Backup the SOLR folder from your installation location in my case it is c:\solr
Navigate to the SOLR installation folder and edit solr.in.cmd file to include: set SOLR_OPTS=%SOLR_OPTS% -Dlog4j2.formatMsgNoLookups=true
Reference:
https://www.prplbx.com/resources/blog/log4j/
Photo by Markus Spiske on Unsplash
Subscribe to Bala Blog | Sitecore MVP | Coveo MVP | DX MVP | Sitecore | Coveo | Microsoft
Get the latest posts delivered right to your inbox

